Cado Protection’s exploration has actually extensively unmasked the idea that macOS systems are unsusceptible malware. This discovery worries a brand-new malware-as-a-service (MaaS) called “Cthulhu Thief,” which targets macOS individuals via deceitful ways.
The surge of Cthulhu Thief suggests that no system is totally safe and secure versus cyber dangers.
Exactly How Malware Swipes Mac Users’ Crypto?
Cthulhu Thief disguises itself as reputable applications such as CleanMyMac and Adobe GenP and software program declaring to be a very early launch of “Grand Burglary Automobile VI.”
Once the individual installs the destructive DMG documents, they are motivated to go into the system and MetaMask passwords. This preliminary deceptiveness is simply the start.
Find Out More: An Overview to the very best AI Safety And Security Solutions in 2024
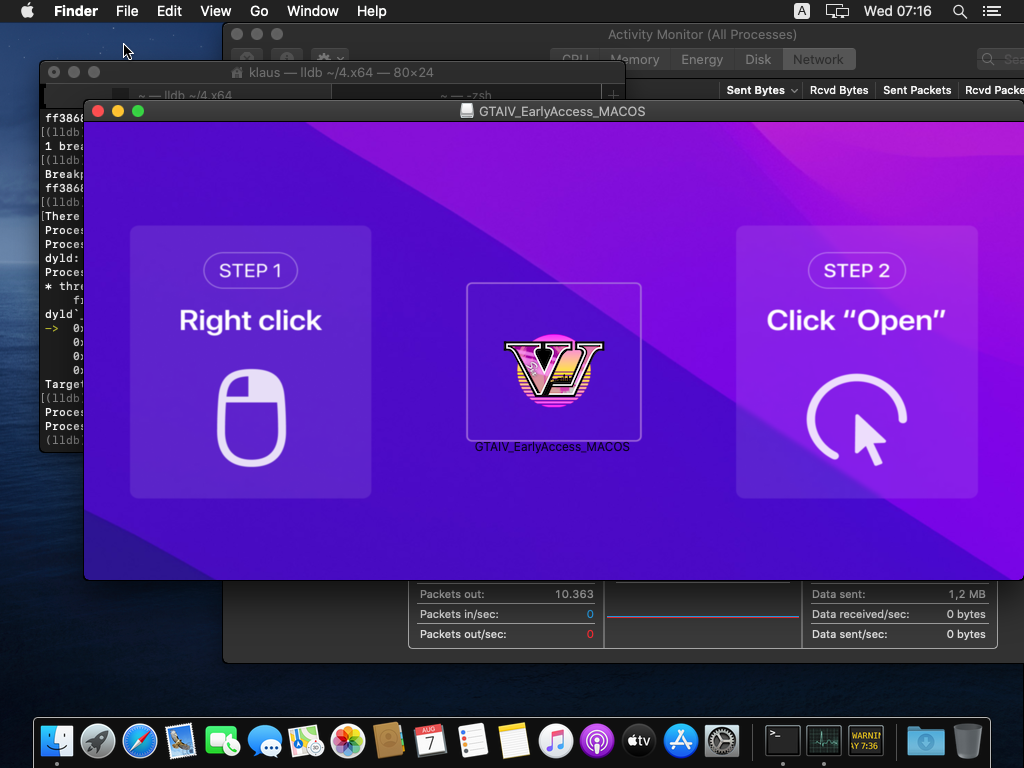
Complying with the qualifications input, the malware makes use of osascript, a macOS device, to draw out passwords from the system’s Keychain. This information, consisting of information from crypto pocketbooks like MetaMask, Coinbase, and Binance, is assembled right into a zip archive. This archive, recognized by the individual’s nation code and the moment of the strike, includes the taken details.
Cthulhu Thief likewise swipes information from various other systems, consisting of:
- Chrome expansion pocketbooks
- Minecraft individual details
- Wasabi purse
- Keychain passwords
- SafeStorage passwords
- Battlenet video game, cache, and log information
- Firefox cookies
- Daedalus purse
- Electrum purse
- Atomic purse
- Consistency purse
- Electrum purse
- Enjin purse
- Hoo purse
- Stylish purse
- Coinomi purse
- Depend on purse
- Blockchain purse
- XDeFi purse
- Web browser cookies
- Telegram Tdata account details
Furthermore, Cthulhu Thief accumulates comprehensive system details such as IP address, system name, and OS variation. It after that sends this information to a command and control (C2) web server, allowing the aggressors to improve their approaches.
Scammers Fee $500/Month For Cthulhu Thief
Fraudsters make use of different approaches to catch the targets right into mounting the malware. As an example, on social media sites, some fraudsters impersonate companies that provide tasks that need downloading software program to track functioning hours. These deals feature a feeling of necessity, pressing the possible target to download and install the application promptly.
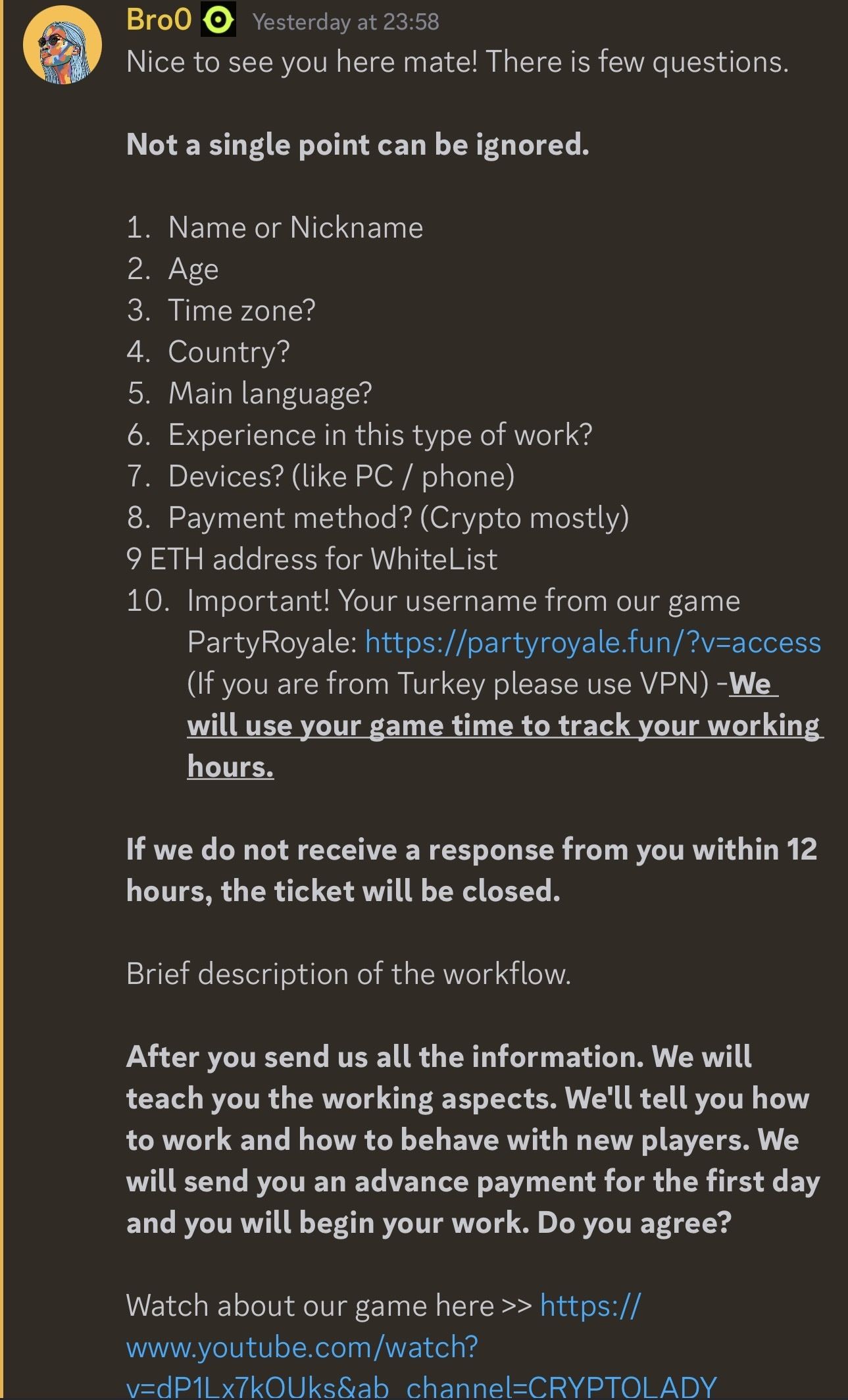
The designers and associates behind Cthulhu Thief, referred to as the Cthulhu Group, usage Telegram to handle their procedures.
” The thief seems being leased to people for $500/month, with the primary designer paying a percent of incomes to associates based upon their release. Each associate of the thief is in charge of the release of the malware. Cado has actually discovered Cthulhu thief marketed on 2 popular malware industries which are utilized for interaction, adjudication and advertising and marketing of the thief, in addition to Telegram,” Cado informed visitors.
Find Out More: 9 Crypto Purse Safety And Security Tips To Secure Your Possessions
To shield themselves, individuals must mount trustworthy anti-viruses software program that is especially developed for macOS. They must likewise beware of job opportunity that need prompt software program downloads. Normal software program updates can even more decrease the danger of malware infections.
Please Note
In adherence to the Depend on Task standards, BeInCrypto is dedicated to honest, clear coverage. This newspaper article intends to give precise, prompt details. Nevertheless, visitors are recommended to confirm truths individually and talk to an expert prior to making any type of choices based upon this material. Please keep in mind that our Conditions, Personal privacy Plan, and Please notes have actually been upgraded.
 Ferdja Ferdja.com delivers the latest news and relevant information across various domains including politics, economics, technology, culture, and more. Stay informed with our detailed articles and in-depth analyses.
Ferdja Ferdja.com delivers the latest news and relevant information across various domains including politics, economics, technology, culture, and more. Stay informed with our detailed articles and in-depth analyses.
